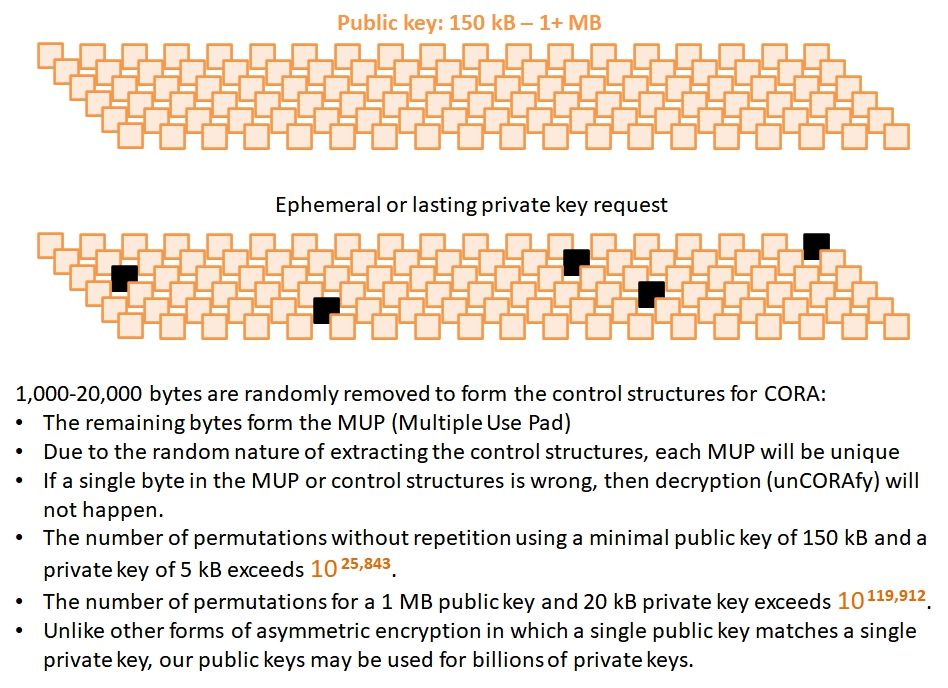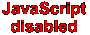
CORA Cyber Security Inc. embraces perfect encryption using Public Keys that support billions of private keys. CORA-X uses a minimum of 150 kB Multiple Use Pad (MUP), resulting in data security that is quantum-safe today and will handle the quantum computers of tomorrow.
A single Public Key corresponds to at most 1 private key.
The public key used by an owner cannot view its own plain text.
Due to attack vectors, the use of ephemeral keys is desired.
Generating ephemeral keys for most Asymmetric algorithms is computationally intensive.
Quantum computers pose a significant risk to factorization based (asymmetric) encryption.
A single CORA Public Key supports billions of private keys.
If desired, a unique public-private key combination may readily encrypt/decrypt plain text.
Probabilistic in nature; everything changes - Public key size, private key size, number of CORA blocs...
The only attack vector is a brute force attack. If a single byte is corrupted or 'different', then decryption will not happen!
Quantum computers will not break CORA since it is not factorization based and involves unimaginable probabilities!
This makes the reliance on ephemeral keys less important. That said, generating ephemeral keys is fast and effective.
CORA: complex probabilities versus complex math.