
CORAcsi is the first to invent, and use a Multiple Use Pad (MUP). MUPs are a practical and reusable form of One Time Pads (OTP), which have long been accepted as the ideal in 'perfect secrecy' according to information theory. While these OTPs have been taught as a theory - since they aren't practical, Latouf has invented a secret sauce that turns OTPs into MUPs, which are practical and reusable.
MUPs break the barriers that exists with finite key size encryption. MUPs are a probabilistic approach to security that allows for a single type of attack � a brute force attack, which due to the astronomically high probabilities, cannot be completed within the life time of our universe (times a trillion).
Imagine a hacker breached your server and stole these 4 CORA blocs.
This hacker will never produce the original 2 images using these 4 CORA blocs!
Even if this hacker somehow obtained all of the CORA blocs, there would still be the MUP to overcome (minimum 1,200,000-bit encryption key).
For faster transfers, such as might be used for real time communication, this next sample uses a single CORA bloc.
Imagine your assembly line is communcating in real time and "someone" gains access to your intranet and records the text that has been CORAfied.
In practice a second bloc could be sent simultaneously via another connection, or channel; just for that 'little extra' in security. Consider a criminal's uncertainty in the # of blocs, size of the MUPs, etc.


Claude Shannon is considered by many to be the father of information theory.
The Claude E. Shannon Award is an coveted honour in the field of information theory.
Shannon introduced, perhaps even originated the concept of "perfect encryption" in 1949.
The concept is known by other names as well:

Current standards in military grade encryption are reported to use 256 - 4096 bit encryption, depending on the type of encryption. Lets say they use

Every single CORAfication of data involves automous CORA blocs, which adheres to Shannon's ideal of perfect encryption using a "one time only, unique key".
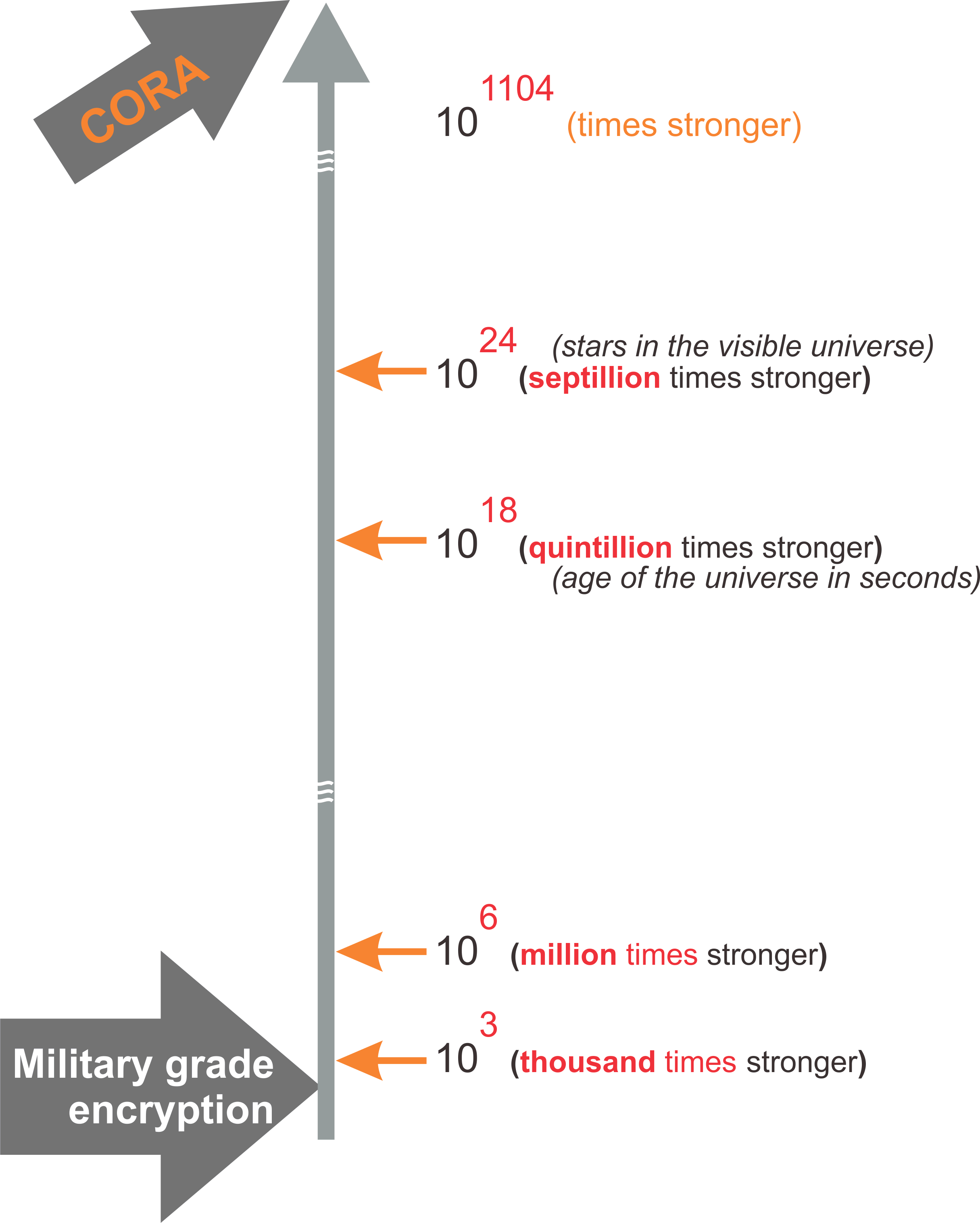
If a brute force attach could break military grade encryption in '1 second',
then it would take 101104 seconds to break CORA.
How big is that?
... it is way more than a googol (zillion, zillion...) times the age of our universe (since the big bang).
Lets put this another way, if military grade encryption is '1 grain of sand', then 101104 is bigger than our entire universe.
That's why it is so much easier to say "unbreakable" !