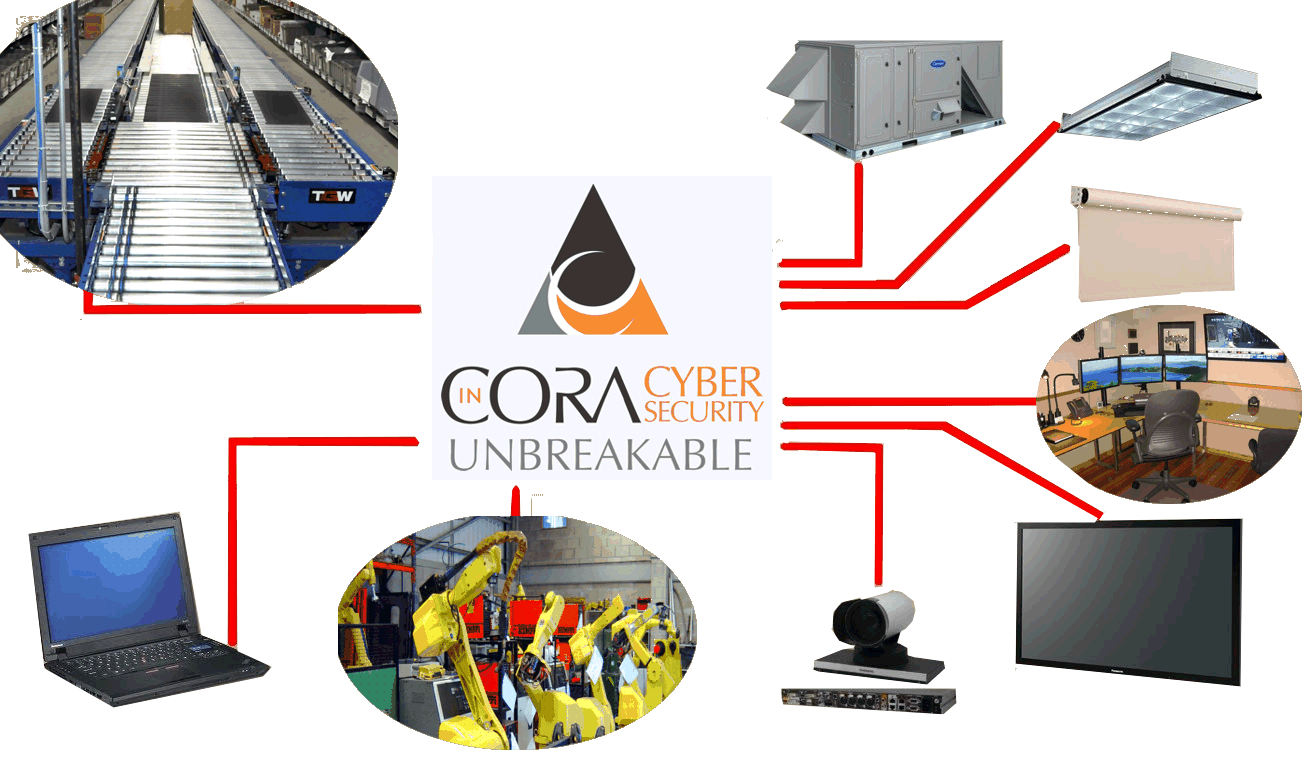
CORA for Industry
CORA's 'trust independent', self-healing technology secures:
- data
- real-time communication
- systems integration
- authentication
- communication
- robotics
- manufacturing
- automation & mobility
- connected vehicles
- the Internet of Things
for companies and organization that need to operate securely and efficiently, 24/7.
perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
Context Order Rendering Algorithm
- CORA decomposes the original file and produces multiple CORA blocs.
- Each bloc essential acts as a "perfect encryption" key.
- All blocs in the CORAfied data are needed to recover the original data.
- Missing a single bloc results in the inability to reproduce 'any part' of the original data.
Context Ordered results in each CORA bloc, and CORA solution, being autonomous; a one-time only unique key.
Replacement Algorithm results in each CORA bloc's size exceeding its proportionate size of the original data.
CORA has been in design and development for more than 5 years. It has matured to a much more robust and dependable implementation that can handle the demands of industrial and commercial applications.
perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
What does 'unbreakable' look like?
Claude Shannon
Claude Shannon is considered by many to be the father of information theory.
The Claude E. Shannon Award is an coveted honour in the field of information theory.
Shannon introduced, perhaps even originated the concept of "perfect encryption" in 1949.
The concept is known by other names as well:
Bottom line: a one-time key that is longer than the data.
perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
Perfect Encryption

Current standards in military grade encryption are reported to use 256 - 4096 bit encryption, depending on the type of encryption.
How does this compare to CORA?

Every single CORAfication of data involves automous CORA blocs, which adheres
to Shannon's ideal of perfect encryption using a "one time only, unique key".
perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
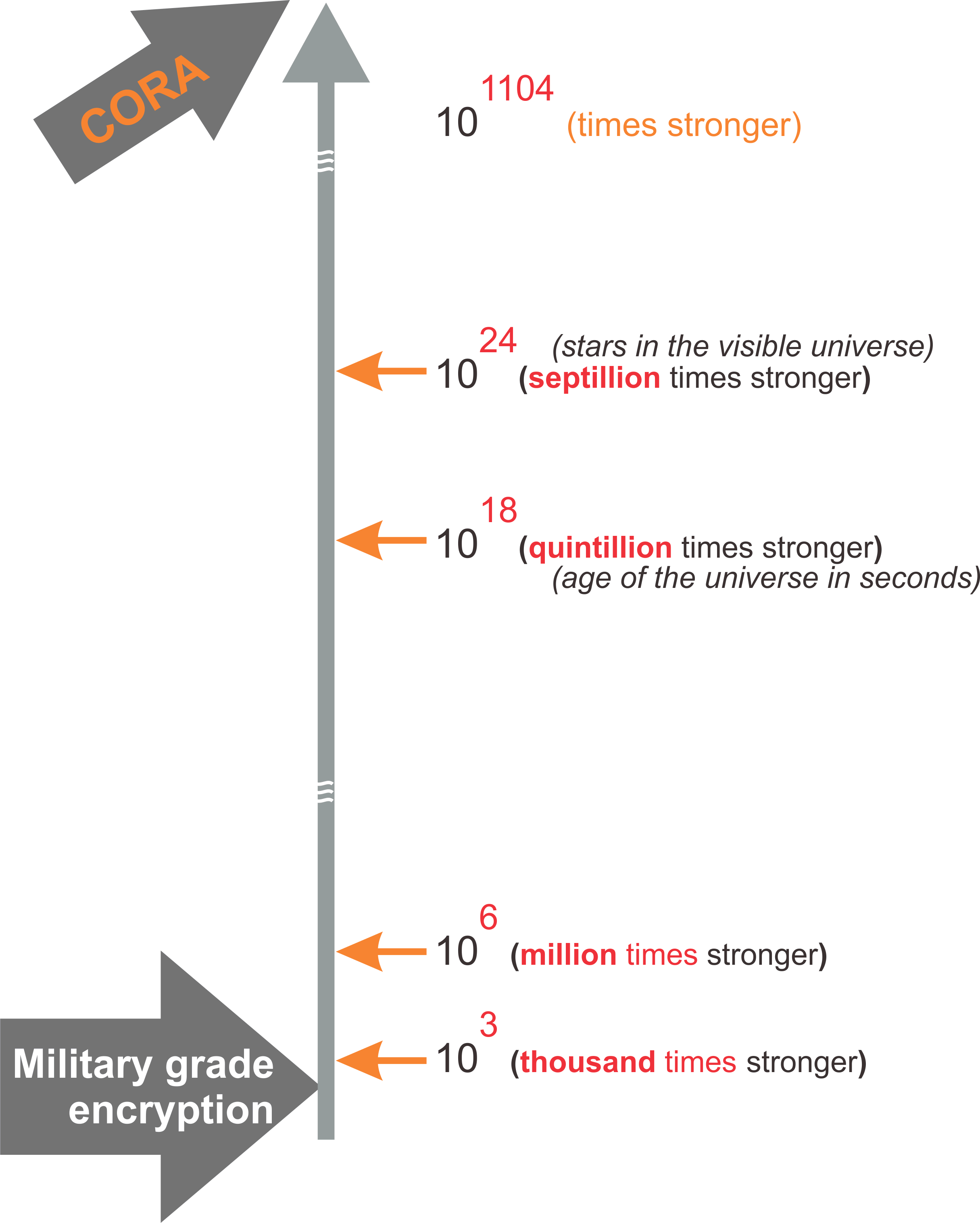
The Math - beyond a googolplex
What is a googol? It is 10100. What's a googolplex? 101000
CORA at its worst is more than 101104 times strong than military grade encryption.
Example
If a brute force attach could break military grade encryption in '1 second',
then it would take 101104 seconds to break CORA.
How big is that?
... it is way more than a googol (zillion, zillion...) times the age of our universe (since the big bang).
Lets put this another way, if military grade encryption is '1 grain of sand', then 101104 is bigger than our entire universe.
That's why it is so much easier to say "unbreakable" !
perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
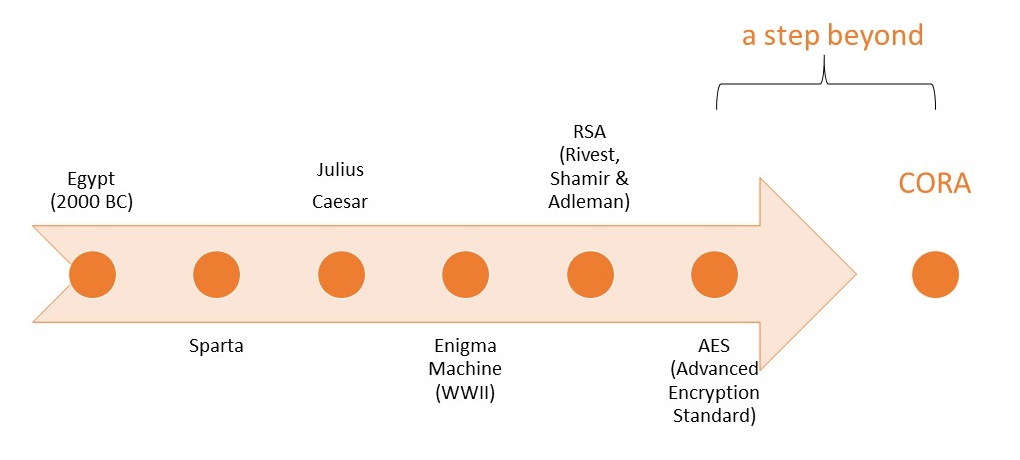
a step beyond encryption
The type of encryption Caesar used was much simpler than the digital encryption we use today. Math and technology has evolved.
While Shannon foresaw 'perfect encryption', it hasn't been implemented - until CORA.
CORA is a step beyond current practices in that it implements a level of protection that has previously, only been dreamed of.
perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
Trust Independent
CORA Cyber Security recognizes that each company, organization, industrial partner desires to have the final say in their security.
- No worries about back doors - do your due diligence,
- No worries about 'who else might have access'.
- No worries if 'your supplier', or 'IT provider' suffers a breach'.
- No dependency on the reliability or integrity of someone else's company or employee.
None of these points replaces 'due diligence' or 'best practices', however, with CORA, if someone hacks your data, the hack will be irrelevant if all they can acquire are numerous / random CORA blocs.

perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
Self-healing
CORA Cyber Security expects that each company and organization will take all necessary precautions to prevent breaches in their security.
That being said, it would be naive to believe that a breach or violation of trust will never occur. CORA was created to address this eventuality.

perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
Chaos Maps and Communication
Chaos Maps are an efficient and powerful method of securing communication (data in transit).
- Robotics
- systems integration
- Industrial controls
- machine to machine
- manufacturing process control
- wifi
- automation & mobility
- the Internet of Things
The keys that efficiently secure the end points of communication are not limited to 256 bits.
perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
CORA Connect (for data in transit)
Overview:
- Produces a single CORA carrier bloc
- End points require the same key(s)
- Unlimited key size
- Variable carrier size
- Multiple keys may be used simultaneously
- Dynamic key capability

perfect secrecy - perfect encryption - CORA unbreakable - 101104 times strong than other encryptions - CORA Connect for Industry, automation and mobility
Failure Analytics
Minimal security profile:
- A single 1 kB key at both end points
- The key remains static during transmissions.
- Minimal carrier length of 1 kB
- The number of possible keys is approximately 102408
- A smart attack involving patterns in random number generators and frequency distributions in byte structures might reduce this to 101926